Backups and Disaster Recovery Health IT Backups are designed to meet standards. The RACGP Accreditation Standard v5 – this is the standard Australian General Practice accredits to. The Essential Eight – published by the Australian Government, these are recommended mitigation strategies against cyber security threats.Health IT’s standard backup products have been designed…
Search Results for:
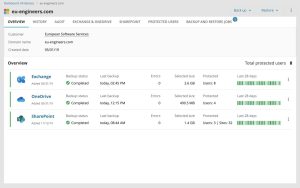
Microsoft Cloud BackupsCentralise your data into the Microsoft system and back it up multiple times a day.Back up ExchangeAutomatically back up Exchange mailboxes including email, contacts, and calendars up to six times a day.Back up SharePoint and OneDriveProtect SharePoint sites and permissions, including custom and sub-libraries, as well as OneDrive…
Site Management – Management of Microsoft 365 Tenancy including security and reporting – Secure Domain and Web Hosting including maintenance, security and minor updates – DMARC email security to prevent email spoofing – Custom Cyber Security Policy aligned to the SMB1001 security standard
Type the Magic Word, Click the Magic Link It’s just that easy. With INKY Email Encryption you don’t have to leave the email system to take action. Simply add the word [encrypt] to the subject line of the email and INKY takes care of the rest. The recipient receives an…
Uplift your Cyber Security – Focus on the Mailbox As technology improves and tools like AI become widely available, cyber security attacks are becoming more sophisticated and increasing in frequency. No longer is it the case that malicious emails are full of spelling mistakes and easy to spot. At Health…
After 14 October 2025, Microsoft will no longer provide free software updates from Windows Update, technical assistance, or security fixes for Windows 10. Your PC will not stop working, but it will no longer be able to be adequately secured. Provided you have a supported version of Windows 10, there…
The ‘What’s New” document that ships with each new version of Best Practice has lots of gems. If you don’t already you should make a habit of reading that. Here two absolute gems in the BP Spectra version. Gem #1 Display unactioned reports in the patient record This gem helps…
The reason why this date of 1 March 2025 is set is shown here https://kb.bpsoftware.net/bppremier/spectra/Clinical/Immunisations/RecordImmunisations.htm The Australian Immunisation Register (AIR) is introducing mandatory changes to simplify the Vaccine Type field. Effective from 01 March 2025, only the following options will be available: NIP/Commonwealth Antenatal Other The options for Private and…
SQL Server is the Microsoft database server that runs underneath Best Practice, Medical Director and many other systems. The free version of SQL Server is sufficient until your medical database is large (10GB). At this time you must upgrade to the paid version or your system will stop working. From…
Disclaimer (IANAL). We are not lawyers and you should not take legal advice from your IT provider. Recently there was a ‘Negligence’ court case in WA that centered around email security. There are three main players, a Consultant, the Company and a Fraudster. Total value of the project was in…