The ‘What’s New” document that ships with each new version of Best Practice has lots of gems. If you don’t already you should make a…
New Year, New Threats For more tips and how-to’s, visit our tech blog Every Financial Year, the Australian Cyber Security Centre posts their Cyber Threat…
What Does “Good” Look Like For a Healthcare Business? For more tips and how-to’s, visit our tech blog Phones Your phones are the primary method for…
7 Ways to keep your family safe online For more tips and how-to’s, visit our tech blog It’s never too early (or late) to learn…
Integrated ECG in BP and MD Risks Data Loss For more tips and how-to’s, visit our tech blog We strive for efficiency in everything we…
What to do when your mobile device is missing or stolen For more tips and how-to’s, visit our tech blog Whether you’ve lost a phone…
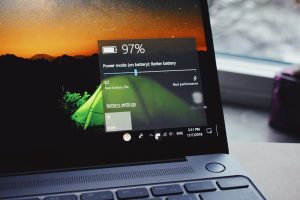
Get More laptop time with these Battery saving tips For more tips and how-to’s, visit our tech blog One of the big draws of a…
Should You Shut Down Your Computer Every Day? For more tips and how-to’s, visit our tech blog Does Shutting Down or Restarting your computer every…
5 Ways hackers target your mobile devices For more tips and how-to’s, visit our tech blog Smartphones and tablets are often the preferred device for communications,…
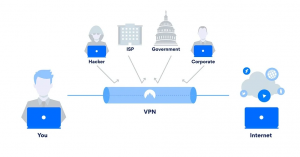
Internet in tubes For more tips and how-to’s, visit our tech blog Virtual Private Networks (VPNs) have been talked about a lot lately whenever the…