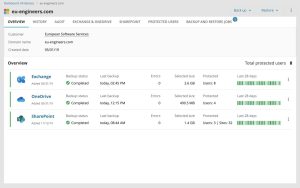
Backups and Disaster Recovery Health IT Backups are designed to meet standards. The RACGP Accreditation Standard v5 – this is the standard Australian General Practice accredits…
Microsoft Cloud BackupsCentralise your data into the Microsoft system and back it up multiple times a day.Back up ExchangeAutomatically back up Exchange mailboxes including email,…
Site Management – Management of Microsoft 365 Tenancy including security and reporting – Secure Domain and Web Hosting including maintenance, security and minor updates –…
Type the Magic Word, Click the Magic Link It’s just that easy. With INKY Email Encryption you don’t have to leave the email system to…
Uplift your Cyber Security – Focus on the Mailbox As technology improves and tools like AI become widely available, cyber security attacks are becoming more…
Disclaimer (IANAL). We are not lawyers and you should not take legal advice from your IT provider. Recently there was a ‘Negligence’ court case in…
New Year, New Threats For more tips and how-to’s, visit our tech blog Every Financial Year, the Australian Cyber Security Centre posts their Cyber Threat…
7 Ways to keep your family safe online For more tips and how-to’s, visit our tech blog It’s never too early (or late) to learn…
Security Update September 2022 For more tips and how-to’s, visit our tech blog Optus Breach You may have seen in the news that Optus were the…
Introducing Health IT Home Security For more tips and how-to’s, visit our tech blog You keep your practice as secure as possible, but what about…