A community of 5.3 billion For more tips and how-to’s, visit our tech blog This webpage takes up about 1 megabyte of space on our server.For context, that’s only about 1/8000th of a USB thumbdrive you might have in your pocket. You could save this page a thousand times before reaching…
Search Results for:
Customise your Yealink phone For more tips and how-to’s, visit our tech blog If you’re finding the default ringtones on your Yealink phone to be a bit bland, you can spice things up by uploading your own custom ringtone.According to Yealink, the ring tone file must be “PCMU audio format,…
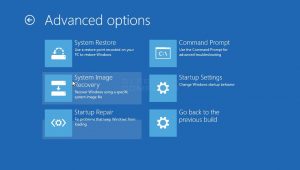
WDF Violation solutions For more tips and how-to’s, visit our tech blog This post is 4 years old. Keep in mind IT is a business of moving targets, and this information may be outdated. Contact Us for more info. Fixing the WDF_VIOLATION on HP computershttps://support.microsoft.com/en-au/help/4468372/hp-devices-may-experience-blue-screen-error-wdf-violation-after-instalTo resolve the WDF_Violation blue screen…
Locate large attachments With one script For more tips and how-to’s, visit our tech blog This post is 4 years old. Keep in mind IT is a business of moving targets, and this information may be outdated. Contact Us for more info. Documents over 50MB are just not cool. They…
If you have a complaint please put it in writing and email it to complaint. Please include as a minimum:Your contact detailsSite nameTicket number if there is an existing ticketYour understanding of the problemThis will generate a Priority 1 job in our system which will be dealt with as soon as…
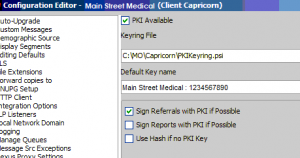
Provider PKI configuration For more tips and how-to’s, visit our tech blog This post is 5 years old. Keep in mind IT is a business of moving targets, and this information may be outdated. Contact Us for more info. Finding your Medical Site Certificate ID in Capricorn You may need…
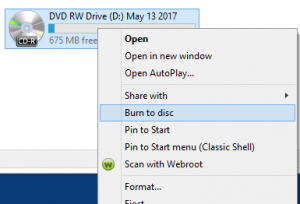
Store patient records on a disk For more tips and how-to’s, visit our tech blog This post is 5 years old. Keep in mind IT is a business of moving targets, and this information may be outdated. Contact Us for more info. Best Practice Export process for patient records to…
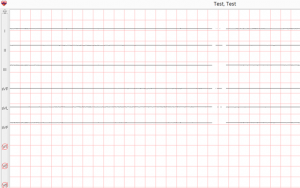
To test before connecting to patient For more tips and how-to’s, visit our tech blog This post is 5 years old. Keep in mind IT is a business of moving targets, and this information may be outdated. Contact Us for more info. A common problem that can happen with any…
How to find out if NBN/ADSL is available in your area For more tips and how-to’s, visit our tech blog This post is 5 years old. Keep in mind IT is a business of moving targets, and this information may be outdated. Contact Us for more info. Use the below…
CLOUD COMPUTING IN PRIMARY HEALTHCARE IN AUSTRALIA Cloud computing certainly sounds like a new phenomenon but it’s been in mainstream use since we embraced Hotmail in 1996. Most of the time, “The Cloud” just means a (virtual) server in a data centre. A data centre is a dedicated home for…